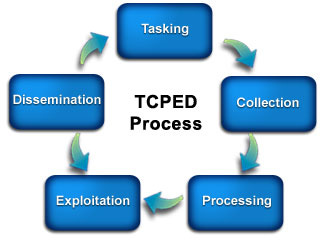
TCPED: The Core Workflow of Geospatial Intelligence
Intelligence Brief: How Tasking, Collection, Processing, Exploitation, and Dissemination Drive Actionable Insights in GEOINT
I was introduced to TCPED in my Geospatial-Intelligence Tradecraft course, and it has proven essential in my own GEOINT and OSINT research, analysis, and reports. Understanding this methodology has not only strengthened my analytical approach but also deepened my appreciation for the structured workflow that drives geospatial intelligence.
Geospatial Intelligence (GEOINT) is an essential discipline that supports decision-making across defense, security, humanitarian aid, and commercial sectors. At its core, GEOINT follows a structured analytical process known as TCPED—Tasking, Collection, Processing, Exploitation, and Dissemination. This workflow ensures that intelligence is systematically gathered, analyzed, and delivered to end-users in a format that drives actionable insights.
For those new to government intelligence workflows but coming from a tech or public-sector background, TCPED provides a structured approach to data-driven decision-making, aligning well with the methodologies used in data science, artificial intelligence, and advanced analytics.
Image Source: FEMA (https://emilms.fema.gov/is_0103/groups/118.html)
Breaking Down TCPED
Each phase of the TCPED cycle plays a crucial role in transforming raw geospatial data into actionable intelligence. Below, we explore these phases in depth, including key technologies, methodologies, and considerations for professionals integrating GEOINT into their work.
1️⃣ Tasking: Defining Intelligence Objectives
Tasking is the problem-definition phase, where intelligence requirements are established. This step involves understanding the operational environment and prioritizing resources effectively.
🔹 Key Elements:
Identifying mission objectives (e.g., monitoring military movements, disaster response, border security).
Defining spatial and temporal parameters.
Assigning resources to specific intelligence priorities.
Coordinating with analysts, policymakers, and field operators.
🔹 Tools & Technologies:
Geospatial Tasking Systems (GTS) – Automates task management for intelligence requirements.
AI-Driven Prioritization – Machine learning models to identify high-priority areas.
Crowdsourced OSINT (Open-Source Intelligence) – Leveraging social media and civilian reports for verification.
Example Use Case: A national security agency wants to track maritime activities near contested waters. Tasking would define the region of interest, specify the need for high-resolution satellite imagery, and prioritize AI-assisted vessel detection.
2️⃣ Collection: Acquiring Data Across Domains
Collection is where data is gathered from various sources, including satellites, UAVs (drones), ground sensors, and open-source intelligence (OSINT). This phase requires balancing classified and unclassified sources to develop a comprehensive intelligence picture.
Key Collection Methods:
Satellite Imagery (Optical, SAR, Hyperspectral) – Capturing visual and radar-based intelligence.
Aerial Reconnaissance – UAVs and aircraft with multispectral sensors.
Human Intelligence (HUMINT) – Interviews, reports from field agents.
OSINT & SIGINT – Analyzing public and intercepted communications.
Tools & Technologies:
Landsat & USGS Earth Explorer – Providing freely available, dated satellite imagery for long-term environmental and infrastructure monitoring.
Sentinel (ESA Copernicus Program) – Delivering high-resolution, multispectral imagery for earth observation.
Google Earth Engine & ArcGIS Pro – For analyzing satellite and aerial imagery. (Note: Google Earth Engine is excellent for exploratory analysis but is not considered precise enough for formal scientific or high-precision intelligence applications.)
Cesium Ion – 3D visualization of terrain and infrastructure. (Note: Cesium provides excellent terrain visualization but lacks dated imagery, making it better suited for broad situational awareness rather than time-sensitive analysis.)
SAR Processing Platforms – For detecting objects through cloud cover and nighttime conditions.
Vector Data Sources – Integrating road networks, infrastructure layers, and demographic data from authoritative sources.
Example Use Case: Monitoring illegal mining operations in protected rainforests using SAR satellites that penetrate dense cloud cover.
3️⃣ Processing: Structuring Data for Analysis
Processing transforms raw geospatial data into structured formats for analysis. This includes data cleaning, georeferencing, and initial categorization.
Key Processing Considerations:
Data Transparency – Machine learning models and algorithms must not function as "black boxes." The methods used to process data should be explainable and reproducible.
Source Vetting – The origin of geospatial data, along with its metadata, must be verified, documented, and reviewed for accuracy.
Change Detection Analysis – Comparing imagery over time to track deforestation, urban expansion, or infrastructure growth.
Geospatial Data Fusion – Integrating satellite, drone, and ground sensor data.
AI & Automation – Using machine learning to process vast datasets in near real-time while maintaining explainability.
Tools & Technologies:
ENVI & Erdas Imagine – Image processing software for remote sensing.
Python (Geopandas, Rasterio) – Automating geospatial data processing.
Cloud-Based Processing (AWS, Google Cloud) – For handling large-scale data.
Example Use Case: Using AI-based feature extraction to automate the detection of military infrastructure changes in foreign territories while ensuring that data sources and model outputs remain auditable.
4️⃣ Exploitation: Deriving Actionable Intelligence
Exploitation is the analytical phase where patterns, trends, and anomalies are identified. This is where intelligence becomes valuable for decision-makers.
Key Exploitation Methods:
Geospatial Predictive Modeling – Forecasting potential events (e.g., troop movements, natural disasters).
Heatmaps & Spatial Analysis – Identifying high-activity zones.
Deep Learning for Image Recognition – Identifying military assets, ships, aircraft from satellite imagery.
Tools & Technologies:
QGIS & ArcGIS Spatial Analyst – Conducting terrain analysis and spatial modeling.
Google Earth Engine – Temporal analysis of climate and environmental factors. (Note: While useful for large-scale environmental monitoring, Google Earth Engine should be supplemented with authoritative datasets for scientific precision.)
NLP (Natural Language Processing) for OSINT – Analyzing large-scale text data to identify geopolitical risks.
Example Use Case: AI-powered object detection models analyzing ports for unusual naval activity, helping security analysts detect unauthorized military buildup while ensuring that machine-learning outputs remain transparent and explainable.
Conclusion: The Impact of TCPED in GEOINT
The TCPED process is the backbone of GEOINT, enabling intelligence professionals to transform raw geospatial data into insights that shape national security, emergency response, and global decision-making. By integrating advanced satellite imagery, AI-driven analytics, and OSINT methodologies, organizations such as the National Geospatial-Intelligence Agency (NGA) and the Department of Homeland Security (DHS) leverage TCPED to ensure mission success.
From monitoring global security threats to assessing environmental hazards, TCPED provides a structured and repeatable approach to intelligence gathering and dissemination. As technology evolves, so too must the TCPED framework—ensuring that geospatial intelligence remains accurate, transparent, and actionable in an increasingly data-driven world.